Configuring ASA Enable and Username Authentication
You would NEVER leave a firewall open so anyone had the ability to log into the device. This defeats the entire purpose of the security device. This lab will discuss and demonstrate the configuration and verification of enable and username authentication.
- Core Knowledge
- Lab Topology
- Initial Configs
- Lab Objectives
- Lab Instruction
Core Knowledge and Real World Scenarios
You would never put a computer that has unrestricted access to corporate servers in the visitors lounge with no password so why in the world would you put a firewall on your network that has no password? That of which the very function of this device is to secure your network from unauthorized access.
The Cisco ASA by default has a blank enable password out of the box and you would be amazed with how many people NEVER change this password or if they do change the password they change it to “cisco” which of course is super secure, sarcastically speaking… When dealing with a Cisco ASA that has no existing configuration, you will be prompted for the Interactive Setup. On the Cisco 5505’s, there will be a basic configuration out of the box to get your ASA working in very little time, however 5510’s or bigger will come with a blank configuration from the factory.
While most enterprises use a Cisco ACS server to control Single Sign On (SSO) utilizing active directory, some company are too small to afford this type of security solution and must go with a simple but secure solution. Commonly this would be either local authentication or Radius via Windows Server to authenticate to Active Directory.
The enable password functions in the same manner as the Cisco IOS enable password. It is a password to authenticate you to access privileged mode of the Cisco ASA from which you can make configuration changes. This command is executed in the same manner as well, enable password PASSWORD
Local username authentication however is a little bit different. You must manually configure console authentication using an AAA statement. So if you want to force people to login to the ASA using a username and password from the local database the following command is required; aaa authentication serial console LOCAL
Keep mind mind that you don’t set a username and password before you execute this command you can get locked out of the Cisco ASA and will be forced to reboot it.
When you log into the ASA using local authentication, you must also re-authenticate to access privileged mode. This can be done by using the enable command and providing the enable password or by the login command and using your credentials if they have level 15 privileges.
CCNA Security Lab 7-8 will demonstrate how to configure SSH to authenticate to a local user database.
Familiarize yourself with the following command(s);
| Command | Description |
|---|---|
| enable password PASSWORD | When executed in global configuration mode, this will set the enable password needed to access privileged mode via the “enable” command. |
| username NAME password PASSWORD privilege 0-15 | This command is executed in global configuration mode to configure local user accounts with specific passwords and privilege levels. |
| aaa authentication serial console LOCAL | This command is executed in global configuration mode to force local user account logins when you connect to the console port of the Cisco ASA |
Lab Logical Topology
The following logical topology is used in all labs found through out Section 7 of the CCNA Security Workbook;
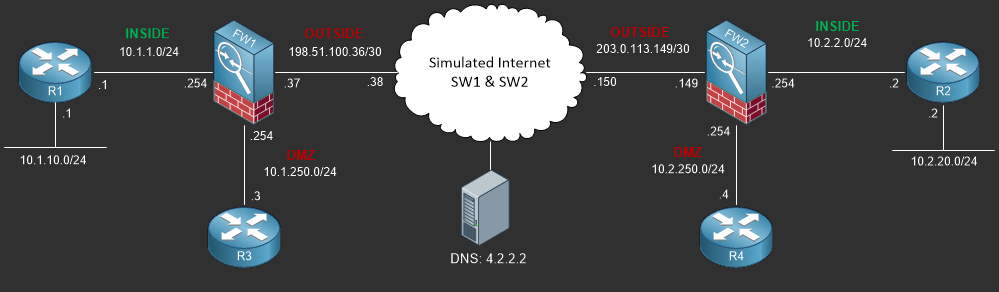
To view the physical cabling topology please visit the Topology page.
Lab Device Initial Configurations
The following initial configuration(s) are provided as a base configuration to start the lab with. You may copy and paste these configurations directly into the terminal window of Stub Lab devices;
Before you Start
This lab requires that you have access to a Cisco ASA. You can complete this lab using a virtual Cisco ASA within GNS3 or you can reserve lab time on the Stub Lab to have free access to Cisco ASA 5505 Series Firewalls which can be used to complete this lab.
Lab Objectives
In this lab you will complete the following objectives.
- Skip the interactive setup and configure the ASA hostname to FW1 and set the enable password to “superman” and verify your configuration.
- Configure a username for the user “jdoe” and the password “whoami” with level 15 privileges.
- Configure console authentication to use the local user database and verify your configuration.
One More Thing…
It is recommended that you attempt to complete these lab objectives the first time without looking at the Lab Instruction section.
If you are a student preparing for the Cisco CCNA Security Certification Exam than you are more likely to remember how to complete these objectives if you attempt to complete them the first time on your own
with the use of the core knowledge section found in this lab. You should only resort to the Lab Instruction section to verify your work.
Lab Instruction
Objective 1. – Skip the interactive setup and configure the ASA Hostname to FW1 and set the enable password to “superman” and verify your configuration.
Pre-configure Firewall now through interactive prompts [yes]? no ciscoasa> enable Password: ciscoasa# config t ciscoasa(config)# hostname FW1 FW1(config)# enable password superman FW1(config)# end FW1# exit Logoff Type help or '?' for a list of available commands. FW1> enable FW1: ******** FW1#
Objective 2. – Configure a username for the user “jdoe” and the password “whoami” with level 15 privileges.
FW1# config t FW1(config)# username jdoe password whoami privilege 15 FW1(config)# end FW1#
Objective 3. – Configure console authentication to use the local user database and verify your configuration.
FW1# config t FW1(config)# aaa authentication serial console LOCAL FW1(config)# end FW1# exit Logoff Username: jdoe Password: ****** Type help or '?' for a list of available commands. FW1> login Username: jdoe Password: ****** FW1#
