Configuring Cisco ASA DHCP Services
The smaller Cisco ASA 5505 is commonly used as a small office firewall and typically most small offices do not have dedicated DHCP Servers so you must configure the firewall to provide DHCP services. This lab will discuss and demonstrate the configuration and verification of DHCP Services on the Cisco ASA Firewall.
- Core Knowledge
- Lab Topology
- Initial Configs
- Lab Objectives
- Lab Instruction
Core Knowledge and Real World Scenarios
Configuring DHCP Services on a Cisco ASA is not common however you may run into this scenario when working with the remote office Cisco ASA 5505 series firewalls. This type of configuration is commonly used at branch offices where no servers are located at.
The Cisco ASA DHCP Daemon operates as a simple DHCP Server providing dynamic IP Addresses, DNS and default gateway information and a domain name if configured. You can get into advanced configurations by providing DHCP options.
The DHCP Daemon is configured on a per interface basis and you specify an address range, not a subnet like you would on Cisco IOS. All of the DHCP services commands start with dhcpd followed by the specific configuration.
To configure a DHCP Scope range, you would use the dhcpd address x.x.x.x-y.y.y.y ifName whereas x.x.x.x is the starting IP Address and y.y.y.y is the ending IP Address and the interface name is specified last.
DNS Servers are configured in the same fashion using the dhcpd dns x.x.x.x y.y.y.y ifName command whereas x.x.x.x is the primary DNS and y.y.y.y is the secondary DNS.
The gateway is automatically set to the interface address. Because of this, the ASA DHCPD has a limited scope of functionality.
After completing the basic DHCP Daemon configuration, you must manually enable the DHCP Daemon on the interface using the dhcpd enable ifName
Familiarize yourself with the following command(s);
| Command | Description |
|---|---|
| dhcpd address x.x.x.x-y.y.y.y ifName | This command is executed in global configuration mode to create a DHCP Daemon scope whereas x.x.x.x is the starting IP Address and y.y.y.y is the ending IP Address and the interface name to which the scope belongs to. |
| dhcpd dns x.x.x.x y.y.y.y ifName | This command is executed in global configuration mode to create set scope DNS servers whereas x.x.x.x is the primary DNS server and y.y.y.y is the secondary DNS Server and the interface name to which the scope belongs to. |
| dhcpd enable ifName | This command is executed in global configuration mode enables the DHCP Daemon on the specified interface. |
Lab Logical Topology
The following logical topology is used in all labs found through out Section 7 of the CCNA Security Workbook;
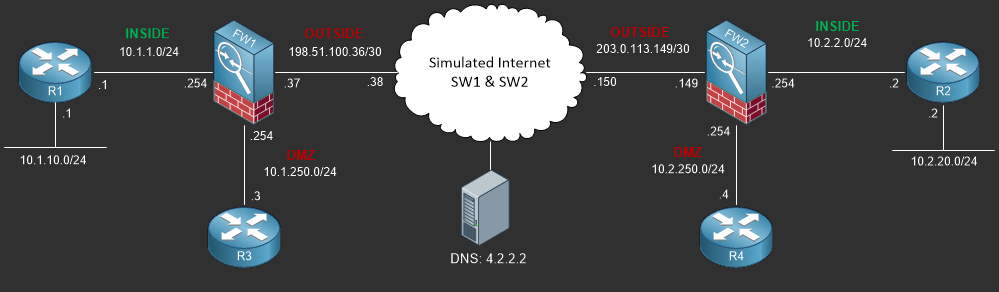
To view the physical cabling topology please visit the Topology page.
Lab Device Initial Configurations
In Section 7 you’ll only be configuring FW1. You will however use other lab devices to verify your configuration on FW1.
If you completed the previous lab you can continue where you left off otherwise you’ll need to load the following initial configurations into their respective device(s);
Section 7 Pre-Configured Lab Device(s)
The following lab devices have been pre-configured to save you time as you’ll only be working with FW1 in Section 7.
In order to complete the labs in section 7 you MUST load the following pre-configuration(s);
Before you Start
This lab requires that you have access to a Cisco ASA. You can complete this lab using a virtual Cisco ASA within GNS3 or you can reserve free lab time on the Stub Lab to have access to a pair of Cisco ASA 5510 Series Firewalls which can be used to complete this lab.
Lab Objectives
In this lab you will complete the following objectives.
- On FW1 configure a DHCP Scope of 10.1.1.10 – 10.1.1.50 on the INSIDE Interface.
- On FW1 configure the DHCP Scope attached to the INSIDE interface to use the DNS Servers of 1.1.1.1 and 2.2.2.2
- Verify that DHCP Services is operational by configuring R1’s FastEthernet0/0 interface as a DHCP client and that it is receiving a default gateway.
One More Thing…
It is recommended that you attempt to complete these lab objectives the first time without looking at the Lab Instruction section.
If you are a student preparing for the Cisco CCNA Security Certification Exam than you are more likely to remember how to complete these
objectives if you attempt to complete them the first time on your own with the use of the core knowledge section found in this lab. You should
only resort to the Lab Instruction section to verify your work.
Lab Instruction
Objective 1. – On FW1 configure a DHCP Scope of 10.1.1.10 – 10.1.1.50 on the INSIDE Interface.
#################################### # UNAUTHORIZED ACCESS PROHIBITED # #################################### Username: cisco Password: ***** ##################################################### # CONTACT JOHN PRIOR TO MAKING ANY CONFIG CHANGES # ##################################################### Type help or '?' for a list of available commands. FW1> en Password: ***** FW1# config term FW1(config)# dhcpd address 10.1.1.10-10.1.1.50 INSIDE
Objective 2. – On FW1 configure the DHCP Scope attached to the INSIDE interface to use the DNS Servers of 1.1.1.1 and 2.2.2.2 and enable the DHCP Daemon on the INSIDE interface.
FW1(config)# dhcpd dns 1.1.1.1 2.2.2.2 interface INSIDE FW1(config)# dhcpd enable INSIDE FW1(config)# end FW1#
Objective 3. – Verify that DHCP Services is operational by configuring R1’s FastEthernet0/0 interface as a DHCP client and that it is receiving a default gateway.
R1>enable R1#config term Enter configuration commands, one per line. End with CNTL/Z. R1(config)#interface FastEthernet0/0 R1(config-if)#ip add dhcp R1(config-if)#end R1# %DHCP-6-ADDRESS_ASSIGN: Interface FastEthernet0/0 assigned DHCP address 10.1.1.10, mask 255.255.255.0, hostname R1 R1# R1#show ip route Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP + - replicated route, % - next hop override Gateway of last resort is 10.1.1.254 to network 0.0.0.0 S* 0.0.0.0/0 [250/0] via 10.1.1.254 1.0.0.0/32 is subnetted, 1 subnets C 1.1.1.1 is directly connected, Loopback0 10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks C 10.1.1.0/24 is directly connected, FastEthernet0/0 L 10.1.1.1/32 is directly connected, FastEthernet0/0 C 10.1.10.0/24 is directly connected, FastEthernet0/1 L 10.1.10.1/32 is directly connected, FastEthernet0/1 R1#
