Preventing Spoofed ARP via Dynamic ARP Inspection
ARP Spoofing is an easy to execute man-in-the-middle attack that can gather a ton of information if left unsecured. By responding to ARP request with a fake MAC address used as a proxy machine, attackers can gather information on your network with ease. This can however be prevented with dynamic ARP inspection, known as DAI.
- Core Knowledge
- Lab Topology
- Initial Configs
- Lab Objectives
- Lab Instruction
Core Knowledge and Real World Scenarios
Spoofing ARP packets is a relatively easy thing to do, anyone with a linux box can do it in a matter of seconds. This however can pose a security risk if the correct ARP packet is spoofed. For example spoofing the ARP packet for the default gateway gives the attacker the ability to become a man-in-the-middle and proxy all traffic destined from clients to the default gateway via layer 2.
This type of attack is another overlooked attack and when executed properly can result in significant damages to intellectual property if the perpetrators intend to sell the intercepted contents.
DAI (Dynamic ARP Inspection) can be configured two main ways with the first being that DAI uses the DHCP Snooping database to verify IP-to-MAC address pairs or by using ARP ACL’s. In this lab you will learn the how to configure DAI using the DHCP Snooping database.
First off, you need to have IP DHCP Snooping enabled and configured on the respected VLAN. Make sure that you have a static database configured located in flash if you intend for the bindings to last if the switch reboots for whatever reason.
After which there is a single simple command to enable DAI which is ip arp inspection vlan #
If you have layer 2 uplink(s) you’ll need to configure those uplink(s) as trusted by using the ip arp inspection trust This command is also needed on devices that act perform proxy arp.
There are a few other things you must know such as ARP rate-limiting build into DAI. By default each untrusted interface is limited to 15 ARP request per second with a 1 second burst rate. Any interfaces exceeding this amount will be placed into ERR-Disabled. This feature is to prevent unwanted DoS attacks on DAI. There is no limit however on trusted interfaces.
There are two show commands you must know, the first being show ip arp statistics which displays DAI statistics on a per vlan basis and show ip arp interfaces which displays which interfaces DAI interface information such as trust state, rate (pps) for arp request and burst interval.
Familiarize yourself with the list of command(s) compiled below;
| Command | Description |
|---|---|
| ip arp inspection vlan {1-4094} | This command when executed in global configuration mode to enable DAI on the configured VLAN. |
| ip arp inspection trust | This command when executed in interface configuration mode sets the interface to trusted and removes the ARP rate limiter, commonly used on up links. |
| show ip arp inspection interfaces | This command when executed in privileged mode displays interface DAI information such as trust state, rate limit pps, burst interval. |
| show ip arp inspection statistics | This command when executed in privileged mode displays information on a per vlan interface regarding DAI. |
To get started with this lab exercise please review the lab topology and prerequisites prior to loading initial configs and attempting the objective(s).
Lab Logical Topology
The following logical topology is used in all labs found through out Section 1 of the CCNA Security Workbook;
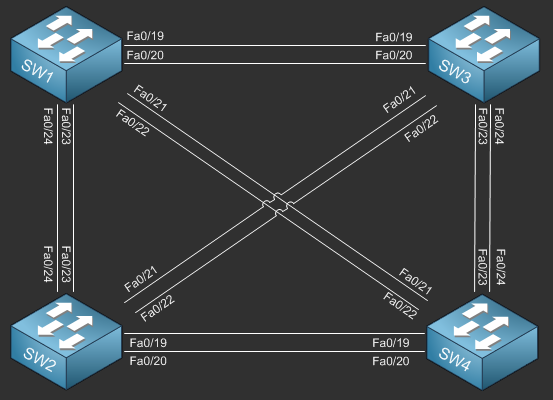
To view the physical cabling topology please visit the Topology page.
Lab Device Initial Configurations
Before you Start
This lab requires that you have access to a real Cisco Catalyst Series Switches. You cannot complete this lab using a NM-16ESW in GNS3. If you do not have a Cisco Catalyst Switch you can reserve free lab time on the Stub Lab to have access to four Cisco Catalyst 3560 Series switches which can be used to complete this lab.
If you completed the previous lab you can continue where you left off otherwise you will need to load the initial configurations provided in the previous tab to complete this lab.
Lab Objectives
In this lab you will complete the following objectives.
- On Dynamic ARP Inspection on SW1 VLAN_1.
- Configure interface FastEthernet0/2 on SW1 to trust all ARP packets.
- Verify your configurations by using show commands.
One More Thing…
It is recommended that you attempt to complete these lab objectives the first time without looking at the Lab Instruction section.
If you are a student preparing for the Cisco CCNA Security Certification Exam than you are more likely to remember how to complete these objectives if you attempt to complete them the first time on your own with the use of the core knowledge section found in this lab. You should only resort to the Lab Instruction section to verify your work.
Lab Instruction
Objective 1. – On Dynamic ARP Inspection on SW1 VLAN_1.
SW1>enable SW1#config t Enter configuration commands, one per line. End with CNTL/Z. SW1(config)#ip arp inspection vlan 1 SW1(config)#
Objective 2. – Configure interface FastEthernet0/2 on SW1 to trust all ARP packets.
SW1>enable SW1#config t Enter configuration commands, one per line. End with CNTL/Z. SW1(config)#interface FastEthernet0/2 SW1(config-if)#ip arp inspection trust SW1(config-if)#end SW1(config)#
Objective 3. – Verify your configurations by using show commands.
SW1#show ip arp inspection interfaces SW1#sh ip arp inspection interfaces Interface Trust State Rate (pps) Burst Interval --------------- ----------- ---------- -------------- Fa0/1 Untrusted 15 1 Fa0/2 Trusted None N/A Fa0/3 Untrusted 15 1 Fa0/4 Untrusted 15 1 Fa0/5 Untrusted 15 1 Fa0/6 Untrusted 15 1 Fa0/7 Untrusted 15 1 Fa0/8 Untrusted 15 1 Fa0/9 Untrusted 15 1 Fa0/10 Untrusted 15 1 Fa0/11 Untrusted 15 1 Fa0/12 Untrusted 15 1 Fa0/13 Untrusted 15 1 Fa0/14 Untrusted 15 1 Fa0/15 Untrusted 15 1 Fa0/16 Untrusted 15 1 Fa0/17 Untrusted 15 1 Fa0/18 Untrusted 15 1 Fa0/19 Untrusted 15 1 Fa0/20 Untrusted 15 1 Fa0/21 Untrusted 15 1 Fa0/22 Untrusted 15 1 Fa0/23 Untrusted 15 1 Fa0/24 Untrusted 15 1 Gi0/1 Untrusted 15 1 Gi0/2 Untrusted 15 1 SW1#show ip arp inspection interfaces Source Mac Validation : Disabled Destination Mac Validation : Disabled IP Address Validation : Disabled Vlan Configuration Operation ACL Match Static ACL ---- ------------- --------- --------- ---------- 1 Enabled Active Vlan ACL Logging DHCP Logging Probe Logging ---- ----------- ------------ ------------- 1 Deny Deny Off Vlan Forwarded Dropped DHCP Drops ACL Drops ---- --------- ------- ---------- --------- 1 0 0 0 0 Vlan DHCP Permits ACL Permits Probe Permits Source MAC Failures ---- ------------ ----------- ------------- ------------------- 1 0 0 0 0 Vlan Dest MAC Failures IP Validation Failures Invalid Protocol Data ---- ----------------- ---------------------- --------------------- Vlan Dest MAC Failures IP Validation Failures Invalid Protocol Data ---- ----------------- ---------------------- --------------------- 1 0 0 0 SW1#
