Protecting the Root Bridge using STP Root Guard
When it comes to layer 2 networks designed in a 3 tier model (core, distro and edge), protecting the spanning-tree root bridge is a must to ensure the security of your network infrastructure.
- Core Knowledge
- Lab Topology
- Initial Configs
- Lab Objectives
- Lab Instruction
Core Knowledge and Real World Scenarios
In most networks, communications between servers on the inside parameter of the network are commonly unencrypted to ensure higher performance however this also includes risk. If an intruder were able to capture this traffic what would they gain from your network?
In a medical environment it could be patient information, history, personal information and more. Perhaps a banking environment could be bank transactions, financial data and so on. The possibilities are endless.
Even in smaller businesses, the risk is often times overlooked. What if your intellectual property was sold to a company in China who started to compete with your business model and ultimately putting you out of business due to cheaper labor cost and lower taxes using intellectual property illegally obtained from your very own company. This type of business warfare is a very profitable business and has occurred several times in the past year alone.
When it comes to the legacy but common 3 tier network where you have a core, distro and edge. Commonly the links between the core and distro are layer 3 and the links between the distro and edge are layer 2.
So lets look at this from a building perspective on a university campus. All this building all distro switches are interconnected via Layer 2 port channels that are trunking and all access switches are linked to the Distro switches via layer 2 links as well. The default gateways for VLAN’s are provided by HSRP on multiple layer 3 distro switches.
From a layer 2 perspective, the two distro switches will be the root primary and secondary for that individual building.
So imagine one day an individual walks into the building doing social engineering pretending to be a University employee and plugs a switch into an active jack on the wall. If BPDU Guard is not enabled and the ports are not configured as static access then the intruder can configure his switch to become a trunk with the access switch and also advertise a higher priority BPDU to also become the root bridge for all VLAN’s. If the intruder is able to successfully execute this attack, what can he gain?
First off he can easily cause several if not complete network degradation. He will also force the existing spanning-tree root to give up its role and forward all unknown traffic towards the new spanning-tree root bridge which the intruder can port-mirror and view in real time using Wireshark.
Protecting the root bridge in a spanning-tree domain is crucial to ensuring layer 2 security. Rood Guard was created by Cisco to provide the ability to securely force the layer 2 switching topology.
Root Guard is configured on trunk uplink interfaces that are from an architectural design never going to become root ports.
With that in mind in this lab you have 3 switches, SW1, SW2 and SW3. SW1 is the root bridge for VLAN’s 1-4094 and all switches are connected together in a full mesh. You will configure Root Guard on SW1 facing SW2 and SW3 because from SW1’s perspective, the interfaces towards SW2 and SW3 WILL NEVER become root ports and this is by design. So by SW1 preventing SW2 and SW3 becoming a root port, it enforces the location of the root bridge in the network.
If SW2 and or SW3 attempt to become the root bridge, SW1 will shutdown the interface towards the offending switch with the error “Root Inconsistent”. If the link between SW2 and SW1 gets disconnected then SW3 will attempt to advertise a a better BPDU to get to the root in which case SW2 will shutdown the link towards SW3 to get to the root. This is by design. While you may think initially this is a bad idea however most access level switches are not capable of handling multi-gigabits of traffic and in by allowing such to happen can cripple both access switches and not just one.
This scenario ensures that any outage to your network is localized and minimized when it comes to spanning-tree root misconfiguration(s) and potential layer 2 attacks.
When it comes to configuring Root Guard, you only need to know a single command which is spanning-tree guard root
Familiarize yourself with the list of command(s) compiled below;
| Command | Description |
|---|---|
| spanning-tree guard root | This command when executed in interface configuration mode disables the interface receives a superior BPDU on this interface. |
To get started with this lab exercise please review the lab topology and prerequisites prior to loading initial configs and attempting the objective(s).
Lab Logical Topology
The following logical topology is used in all labs found through out Section 1 of the CCNA Security Workbook;
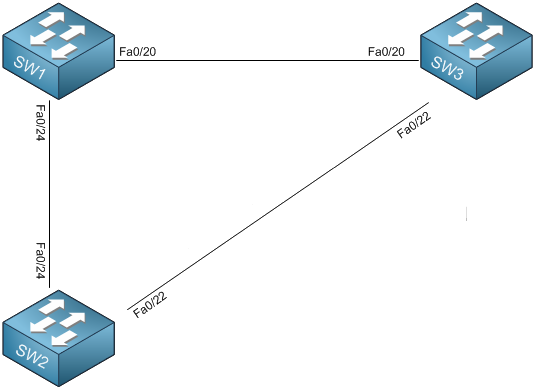
To view the physical cabling topology please visit the Topology page.
Lab Device Initial Configurations
The following initial configurations are provided as a base configuration to start the lab with. You may copy and paste these configurations directly into the terminal window of Stub Lab devices.
Before you Start
This lab requires that you have access to Cisco Catalyst Switches. You cannot complete this lab using the NM-16ESW in GNS3. You can however reserve free lab time on the Stub Lab to have access to a four Cisco Catalyst 3560 Series switches.
Load the initial configuration provided in this lab by copying and pasting them into the terminal window of their respected device(s).
Lab Objectives
In this lab you will complete the following objectives.
- On SW1 configure spanning-tree root guard on trunk links connected towards SW2 and SW3
- Configure Root Guard on the trunk link between SW2 and SW3.
One More Thing…
It is recommended that you attempt to complete these lab objectives the first time without looking at the Lab Instruction section.
If you are a student preparing for the Cisco CCNA Security Certification Exam than you are more likely to remember how to complete these objectives if you attempt to complete them the first time on your own with the use of the core knowledge section found in this lab. You should only resort to the Lab Instruction section to verify your work.
Lab Instruction
Objective 1. – On SW1 configure spanning-tree root guard on trunk links connected towards SW2 and SW3
SW1>enable SW1#config t Enter configuration commands, one per line. End with CNTL/Z. SW1(config)#interface fa0/20 SW1(config-if)#spanning-tree guard root SW1(config-if)#interface Fa0/24 SW1(config-if)#spanning-tree guard root SW1(config-if)#exit SW1(config)#
Objective 2. – Configure Root Guard on the trunk link between SW2 and SW3.
SW2>enable SW2#config t Enter configuration commands, one per line. End with CNTL/Z. SW2(config)#interface fa0/22 SW2(config-if)#spanning-tree guard root SW2(config-if)#exit SW2(config)#
SW3>enable SW3#config t Enter configuration commands, one per line. End with CNTL/Z. SW3(config)#interface fa0/22 SW3(config-if)#spanning-tree guard root SW3(config-if)#exit SW3(config)#
