Configuring ASDM Management Access
Configuring the Cisco ASA for remote ASDM management access which allows you to manage your Cisco ASA firewall via the Cisco ASDM GUI.
- Core Knowledge
- Lab Topology
- Initial Configs
- Lab Objectives
- Lab Instruction
Core Knowledge and Real World Scenarios
Throughout history Cisco has made many attempts at providing a GUI for engineers to configure their hardware on however 99% of all skilled engineers prefer command line over the GUI because of the simplicity and the ability to get right to the point.
For example, lets say you need to view which servers are included in an object group on a Cisco ASA. You could either load up the ASDM and authenticate and wait for the GUI to load, than click on configuration than navigate to the object-groups and find the object group down through the list just to view the servers in the group or you could simply log into the ASA via SSH and execute the show run object-group | begin NAME whereas the name is the name of the object group. Effectively saving 3-5 minutes of your time thus making you more productive. Now imagine you do this multiple times a day… You could easily save 30 minutes or more a day just by avoiding the ASDM to do simple task versus the command line.
While most engineers prefer command line, there are those select few who would prefer to point and click. In many organizations you have those who prefer GUI and those who prefer ASDM. While this is not a problem, the ASDM does tend to make the configuration harder to read because of the naming convention it uses. Many corporate security policies require that the ASDM be completely uninstalled from the ASA as an effective measure of hardening the device due to the software utilizing JAVA which is constantly being updated due to bugs, exploits and security vulnerabilities.
In any case, for the CCNA Security and CCNP Security exams you must be familiar with the Cisco ASDM, this of course does not mean you have to use it to manage your firewalls.
The Cisco ASDM software for the ASA’s is actually a binary file that is a zipped up JAR file for a web browser. The Cisco ASDM is completely Java based and whenever a new ASA software is released, a new ASDM image is released along with it to ensure its compatibility. Newer ASDM images are compatible with previous ASA software however older ASDM binaries are not compatible with newer firewall software. This is because commands may have changed between the time the supports firewall software was released and the latest software.
When configuring the Cisco ASDM on the ASA, you must specify the path in command line as to the location of the binary file. This is done via the asdm image disk0:/asdm-XYZ.bin command whereas XYZ is the ASDM version. X being the Major Release, Y being the minor release and Z being the rebuild revision.
As with configuring SSH, you must also ensure that the ASDM can authenticate to the local user database which is done by using the aaa authentication http console LOCAL command.
The last step in configuring your firewall to permit ASDM access is to enable the HTTP Server via the http server enable command.
Familiarize yourself with the following command(s);
| Command | Description |
|---|---|
| asdm image disk0:/asdm-XYZ.bin | This command is executed in global configuration mode to set the ASDM image location. The ASDM will not function without this configuration. |
| aaa authentication http console LOCAL | This command is executed in global configuration mode to make ASDM authenticate to the local user database. |
| http server enable | This command is executed in global configuration mode enables the HTTP Daemon used by ASDM. |
Lab Logical Topology
The following logical topology is used in most labs found through out Section 7 of the CCNA Security Workbook;
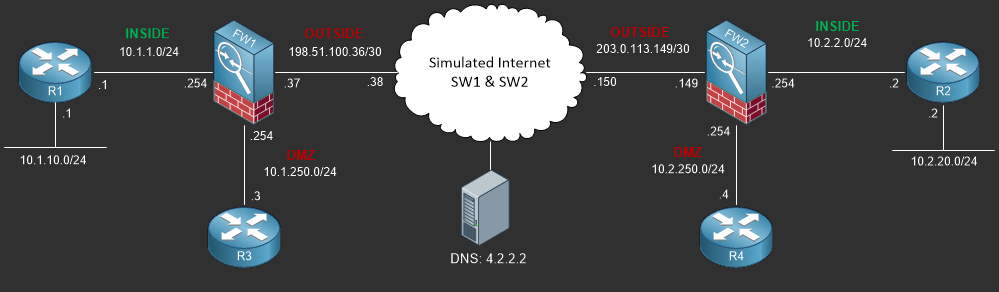
To view the physical cabling topology please visit the Topology page.
Lab Device Initial Configurations
In Section 7 you’ll only be configuring FW1. You will however use other lab devices to verify your configuration on FW1.
If you completed the previous lab you can continue where you left off otherwise you’ll need to load the following initial configurations into their respective device(s);
Section 7 Pre-Configured Lab Device(s)
The following lab devices have been pre-configured to save you time as you’ll only be working with FW1 in Section 7.
In order to complete the labs in section 7 you MUST load the following pre-configuration(s);
Before you Start
This lab requires that you have access to a Cisco ASA. You can complete this lab using a virtual Cisco ASA within GNS3 or you can reserve free lab time on the Stub Lab to have access to a pair of Cisco ASA 5510 Series Firewalls which can be used to complete this lab.
Lab Objectives
In this lab you will complete the following objectives.
- On FW1 configure the ASDM file location and local HTTP authentication.
- Configure FW1 so that the subnet 10.1.0.0/16 is permitted to access ASDM on the INSIDE interface and enable the http server.
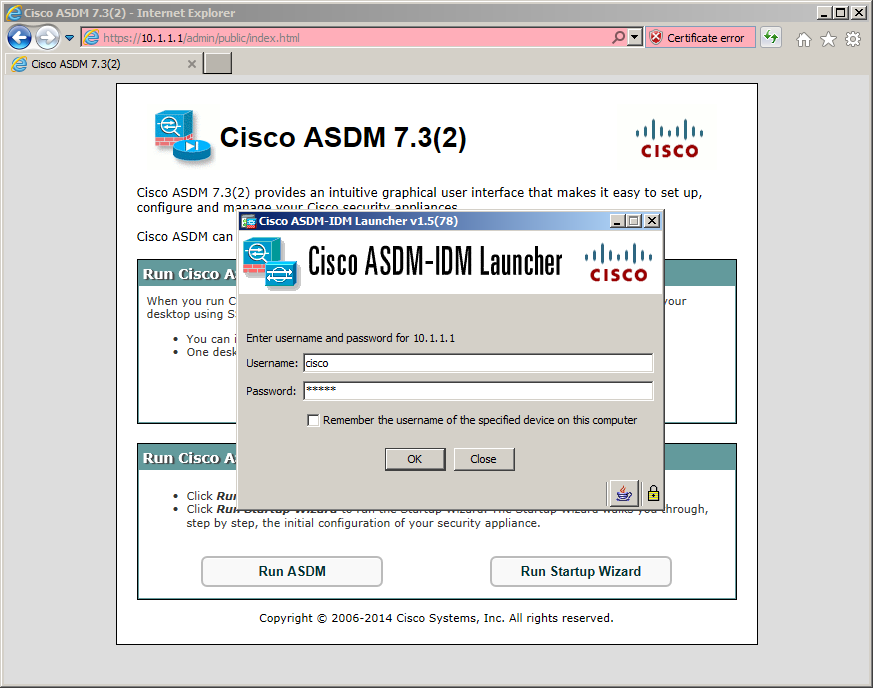
- Verify that you’re able to connect to the Firewall via ASDM using Internet Explorer and the the cisco/cisco credentials.
One More Thing…
It is recommended that you attempt to complete these lab objectives the first time without looking at the Lab Instruction section.
If you are a student preparing for the Cisco CCNA Security Certification Exam than you are more likely to remember how to complete these objectives if you attempt to complete them the first time on your own with the use of the core knowledge section found in this lab. You should only resort to the Lab Instruction section to verify your work.
Lab Instruction
Objective 1. – On FW1 configure the ASDM file location and local HTTP authentication.
#################################### # UNAUTHORIZED ACCESS PROHIBITED # #################################### Username: cisco Password: ***** ##################################################### # CONTACT JOHN PRIOR TO MAKING ANY CONFIG CHANGES # ##################################################### Type help or '?' for a list of available commands. FW1> en Password: ***** FW1# config t FW1(config)# asdm image FW1(config)# asdm image flash:asdm-732.bin FW1(config)# aaa authentication http console LOCAL FW1(config)#
Objective 2. – Configure FW1 so that the subnet 10.1.0.0/16 is permitted to access ASDM on the INSIDE interface and enable the http server.
FW1(config)# http 10.1.0.0 255.255.0.0 INSIDE FW1(config)# http server enable FW1(config)# end FW1#
Objective 3. – Verify that you’re able to connect to the Firewall via ASDM using Internet Explorer and the the cisco/cisco credentials.
You have two options, either install the ASDM client on your local machine which requires administrative rights or clicking on “Run ASDM”. For this lab click on “Run ASDM” and you’ll be promoted to verify the website’s certificate and confirm that you wish to execute the JAVA applet, confirm these actions until you are prompted for the username and password.