Disabling Dynamic Trunking Protocol (DTP)
When it comes to securing the network one of the most overlooked items is Dynamic Trunking Protocol, also known as DTP. This Cisco proprietary protocol is used to negotiate trunk links between VLAN aware Cisco switches using Dot1q or ISL and is commonly enabled by default. This lab will go into details regarding DTP and how to deal with this protocol from a security perspective.
- Core Knowledge
- Lab Topology
- Initial Configs
- Lab Objectives
- Lab Instruction
Core Knowledge and Real World Scenarios
When it comes to modern Cisco switches, most brand new Cisco switches out of the box have Dynamic Trunking Protocol enabled on each port by default. DTP is a simple layer 2 protocol used to negotiate trunk links between Cisco switches. The negotiation process will also determine which trunking protocol is used between the two switches which will be either Dot1q or ISL. By default if no trunking encapsulation is configured on either end, ISL will be negotiated if supported by each switch.
DTP has two modes, dynamic auto and dynamic desirable.
Dynamic Auto which is the default for Cisco 3560’s and later will not attempt to negotiate a trunk link however will negotiate a trunk link if the other end is requesting one.
Dynamic Desirable is the default for Cisco 3550 Series switches and will attempt to actively negotiate a trunk link between its neighboring switch. If the neighboring switch(s) have DTP auto or desirable, a trunk link will be created using the negotiated isl trunking protocol.
One of the most important commands to determine information regarding switchport DTP status is show interface trunk
The following is an example of the command of the show interfaces trunk command on a Cisco 3560 Switch;
SW1#show interfaces trunk
Port Mode Encapsulation Status Native vlan
Fa0/23 desirable n-isl trunking 1
Port Vlans allowed on trunk
Fa0/23 1-4094
Port Vlans allowed and active in management domain
Fa0/23 1
Port Vlans in spanning tree forwarding state and not pruned
Fa0/23 1
SW1#
As you can see from the example, several key pieces of information is provided by this show command. The interface names and their DTP status as listed under Mode, the encapsulation used on the trunk interface. In this case DTP id desirable and is negotiating an ISL Trunk with the neighboring switch and the native vlan is 1.
Taking a step back lets look at the security repercussions from DTP negligence.
By leaving default configurations on Catalyst switchport(s) you’re putting your network at risk by allowing a potential intruder to plug in a switch configured at dynamic desirable. This will negotiate a trunk between your network switch and the attackers switch. At this point the attacker has visibility into all VLAN’s passing traffic on that trunk interface. From here an attacker can easily use packet analysis software to execute recon and gather crucial information on your network regarding IP addressing, host names, DNS servers and any other type of traffic that can be identified by analyzing a broadcast frame.
There are two ways to disable DTP and from an architectural perspective, DTP should never be allowed to remain on by default.
The first way is configuring the switchport as an access port by using the command switchport mode access. This will disable DTP and allow the switchport to operate only in the configured VLAN, if none is configured by default it will be placed into VLAN_1.
The second way to disable DTP is by using the command switchport nonegotiate statically configured trunk interfaces. This will ensure that DTP is disabled and static trunking is configured. This is the most common way to configure trunk unlink s between switches to share layer 2 information.
Familiarize yourself with the list of command(s) compiled below;
| Command | Description |
|---|---|
| show interfaces trunk | This command when executed in user/privileged mode displays information regarding DTP and trunking status on their respective interface(s). |
| switchport mode access | This command when executed in interface configuration mode disables DTP by statically placing the interface into the configured vlan. |
| switchport nonegotiate | This command when executed in interface configuration mode disables DTP on statically configured trunking interfaces. |
To get started with this lab exercise please review the lab topology and prerequisites prior to loading initial configs and attempting the objective(s).
Lab Logical Topology
The following logical topology is used in all labs found through out Section 1 of the CCNA Security Workbook;
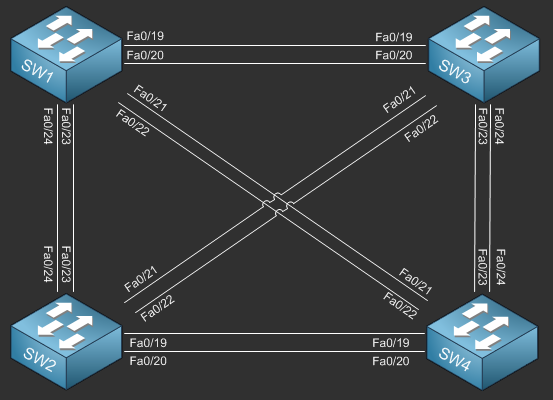
To view the physical cabling topology please visit the Topology page.
Lab Device Initial Configurations
The following initial configurations are provided as a base configuration to start the lab with. You may copy and paste these configurations directly into the terminal window of Stub Lab devices.
Before you Start
This lab requires real Cisco Switches. You can reserve lab time on the Stub Lab to have free access to Cisco Catalyst 3560 Series switches which can be used to complete this lab. To make things easier you may load the initial configurations provided in this lab as a base config.
Please note that this lab cannot be performed in GNS3 using the NM-16ESW.
Lab Objectives
In this lab you will complete the following objectives.
- On SW1, configure Fa0/23 to negotiate a trunk with SW2 via DTP.
- On SW1 configure Fa0/24 as a static trunk interface and disable DTP.
- Verify your configurations by viewing the DTP status of Fa0/23 and Fa0/24.
Before you Continue
It is recommended that you attempt to complete these lab objectives the first time without looking at the Lab Instruction section.
If you are a student preparing for the Cisco CCNA Security Certification Exam than you are more likely to remember how to complete these objectives if you attempt to complete them the first time on your own with the use of the core knowledge section found in this lab. You should only resort to the Lab Instruction section to verify your work.
Lab Instruction
Objective 1. – On SW1, configure Fa0/23 to negotiate a trunk with SW2 via DTP.
SW1>enable SW1#config t Enter configuration commands, one per line. End with CNTL/Z. SW1(config)#interface fa0/23 SW1(config-if)#switchport mode dynamic desirable SW1(config-if)#exit SW1(config)#
Objective 2. – On SW1 configure Fa0/24 as a static trunk interface and disable DTP.
SW1(config)#interface fa0/24 SW1(config-if)#switchport trunk encapsulation dot1q SW1(config-if)#switchport mode trunk SW1(config-if)#switchport nonegotiate SW1(config)#
Objective 3. – Verify your configurations by viewing the DTP status of Fa0/23 and Fa0/24.
SW1#show interfaces trunk
Port Mode Encapsulation Status Native vlan
Fa0/23 desirable n-isl trunking 1
Fa0/24 on 802.1q trunking 1
Port Vlans allowed on trunk
Fa0/23 1-4094
Fa0/24 1-4094
Port Vlans allowed and active in management domain
Fa0/23 1
Fa0/24 1
Port Vlans in spanning tree forwarding state and not pruned
Fa0/23 none
Fa0/24 none
SW1#
